Today most applications require users to authenticate to their account by asking them email/username and password. The user-entered password is matched with the password stored in the database, and if they matched correctly the user is authenticated into their account. Have you thought about what would happen if the database containing these confidential credentials gets compromised by hackers? Does the hacker get access to all user accounts?
In this article, we’ll discuss why to store passwords securely in the databases, important techniques like hashing, salting, iterations for storing passwords securely, and their significance.
Passwords in Plain Text
Let’s say we have a database containing login credentials for our users. A hacker manages to break into our database and has access to all login details (Login, Password).
| login | password |
|---|---|
| john | helloworld |
| curiousfox | golden |
| happylion | q~#:p*‘ZNkA; |
| cutepanda | 123456 |
| littlefox | golden |
Table 1 - Passwords in Plain Text
In this case, the hacker can access all passwords in plain text. Even though happylion has a strong password, his account is not protected.
Passwords should never be stored in plain text. Passwords are such sensitive and confidential information that should not be accessed (in plain text) by anyone including the website administrators.Encrypted Passwords
Passwords should be securely stored in an encrypted or hashed format in the database, ensuring they do not directly represent the actual password.
Passwords are mainly stored in two encrypted forms in a database:
- Reversible algorithm
- Irreversible algorithm
Reversible encryption algorithms, such as ROT13, AES, DES, and others, are designed in such a way that they can be decrypted back into their original values. This makes reversible encryption algorithms ineffective for storing the passwords in the database.
As a result, it is recommended to store the passwords in the database with irreversible encryption algorithms.
Hash Functions
Password hashing with common hash functions (md5, sh1, etc) is an irreversible cryptographic technique to hash the passwords and securely store the passwords in the database. The major downside of using them is that today’s computational power makes hashing vulnerable as it can be easily guessed.
Let’s look at the hash of the passwords in Table 1:
| login | password |
|---|---|
| john | 6adfb183a4a2c94a2f92dab5ade762a47889a5a1 |
| curiousfox | ec30adc79e734900430e4174cf0a36c2d0c42272 |
| happylion | ec44b36634c9bf7f5aec72e4dcdc403393b13fad |
| cutepanda | 7c4a8d09ca3762af61e59520943dc26494f8941b |
| littlefox | ec30adc79e734900430e4174cf0a36c2d0c42272 |
Table 2: SHA1 Hashed Passwords
Here as we can see the passwords are now hashed and obscuring the original content. These hashed passwords would look unfamiliar to normal users, but attackers are very familiar with them and can easily unhash these passwords.
A simple Google search of the hashes allows retrieving the original password.
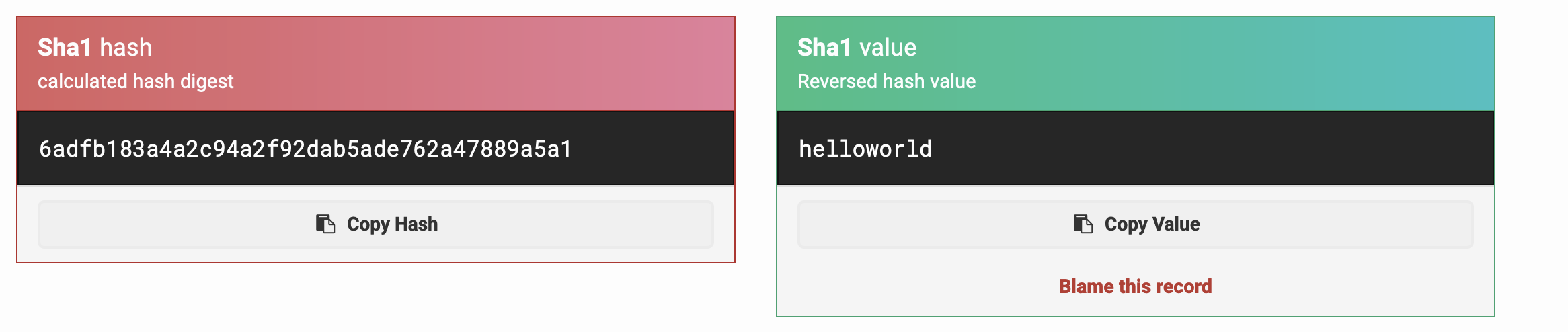
[Caption: In this case, John’s password is easily retrieved.]
- In the case of happylion it would be difficult to retrieve the password from the hash as it is a very uncommon and strong password. While others have very simple and common passwords (e.g. 10-million-password-list-top-10000.txt) making them more vulnerable.
- It is also important to note that, curiousfox and littlefox both share the same hash as they have the same password. Hashes don’t have any randomness and make the user accounts vulnerable to sharing identical passwords.
If the hashes are not found directly using some online tool/search engine, attackers can try the following methods to retrieve the password.
Brute force Attack
A brute force attack is a hacking method that relies on a trial-and-error approach to guess a password. It’s one of the most common techniques used by hackers to gain unauthorized access to accounts by repeatedly trying different combinations of characters until they discover the correct password. Think of it like trying every possible combination, such as starting with 0000, then 0001, 0002, and so on, until you find the right passcode for your mobile phone.
“In our case, hackers attempt to guess passwords by hashing common ones (like those in the rockyou.txt list) and comparing the resulting hash values with the stored SHA1 hashed passwords in our database. If they find a match, they can uncover the actual password. This is why brute force attacks can undermine the security provided by hashing.”
Dictionary Attack
A dictionary attack is a method used by hackers to guess passwords by systematically trying a large list of words, phrases, or common passwords from a predefined “dictionary.” It’s a bit like flipping through the pages of a dictionary to find a word.
Here’s how it works:
- The attacker has a list of words, phrases, or commonly used passwords, which could be obtained from various sources like known password databases or commonly used words.
- The attacker then systematically tries each item in the list as a potential password.
- They compare these items to the hashed passwords stored in a database. If they find a match, it means they’ve successfully guessed the password.
Dictionary attacks can be of the following types:
- Using the most common passwords
- Language dictionary
- Phrases from the given context
This means that if the user’s name is “John”, the attacker will try to find his birthday, pet’s name, favorite food, or any other thing related to him. This way the attacker can crack the password.
Rainbow Table
A Rainbow Table is a precomputed table of password hashes that are used to crack the password in the database.
As we discussed earlier, hashing every password in the wordlist and matching them with the hash is a very slow process to crack the password. That is where the rainbow tables have been introduced. Rainbow tables are a way to speed up this process. They are precomputed tables that contain pairs of possible passwords and their corresponding hash values. These tables are generated in advance using various combinations of passwords and hash functions. So, when an attacker wants to crack a hashed password, they can quickly look it up in the rainbow table to find the corresponding plaintext password.
As we’ve explored the techniques that attackers can use to crack a user’s real password, it’s important to turn our attention to the solutions that can help enhance security and protect against these threats.
Salting
The vanilla SHA512 hash is not suitable for password storage. If we mix some random characters with the original password and then hash it will create a unique hash that makes it nearly impossible to crack the real passwords. Each user will have a unique salt, consisting of a randomly generated sequence of characters. This makes the password hash of every user to be totally unique in the database.
So, even if the littlefox and curiousfox share the same password, they will have different and unique salts resulting in a different hash in the database.
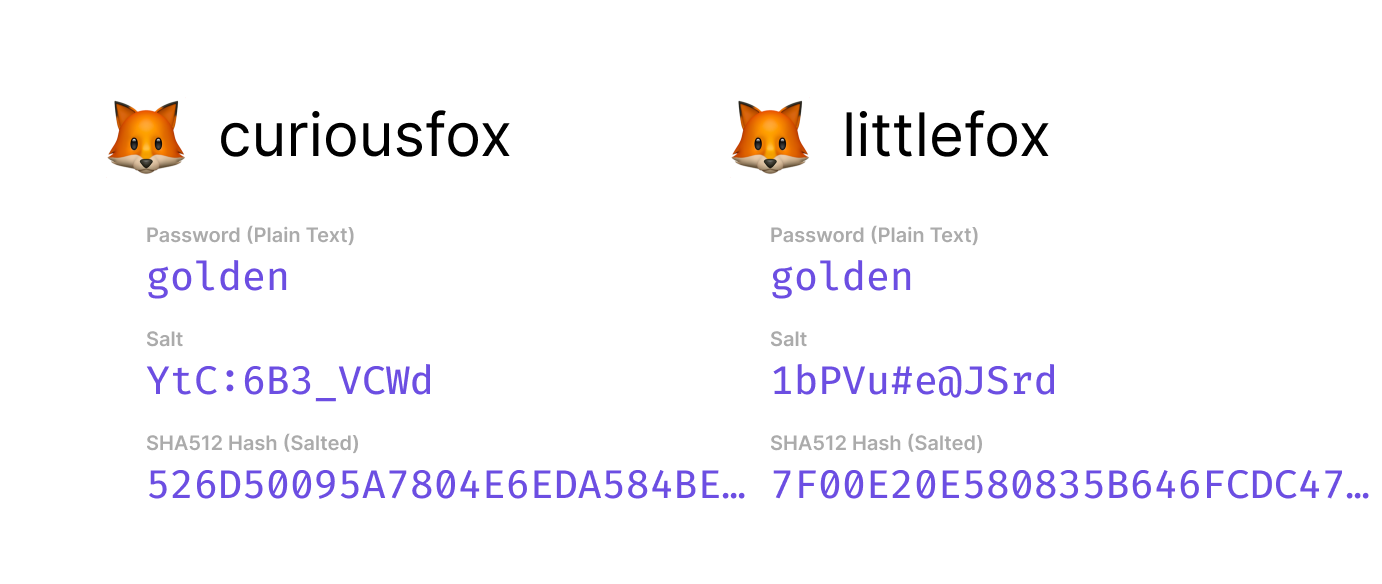
The advantages of salting:
- It is nearly impossible to find the hash directly on the internet if it is salted.
- Rainbow tables are not effective against the salted hashes.
- Even though users sharing the same password will not have the same hash. However, the salt must be unique and randomly generated.
Increase the number of iterations
Increasing the number of iterations means the password is going to be hashed n number of times. Increasing the iterations helps improve the security of the hash and makes it harder for the hacker to crack the hash.
Now, think of it this way: instead of just one round of this hashing marathon, you decide to go all out and repeat it a whopping 10,000 times. That’s like slapping a bunch of locks on a door. You know, the more locks, the more hassle for anyone trying to break in. It’s like turning your password into a fortress that’s not so easy to trespass.
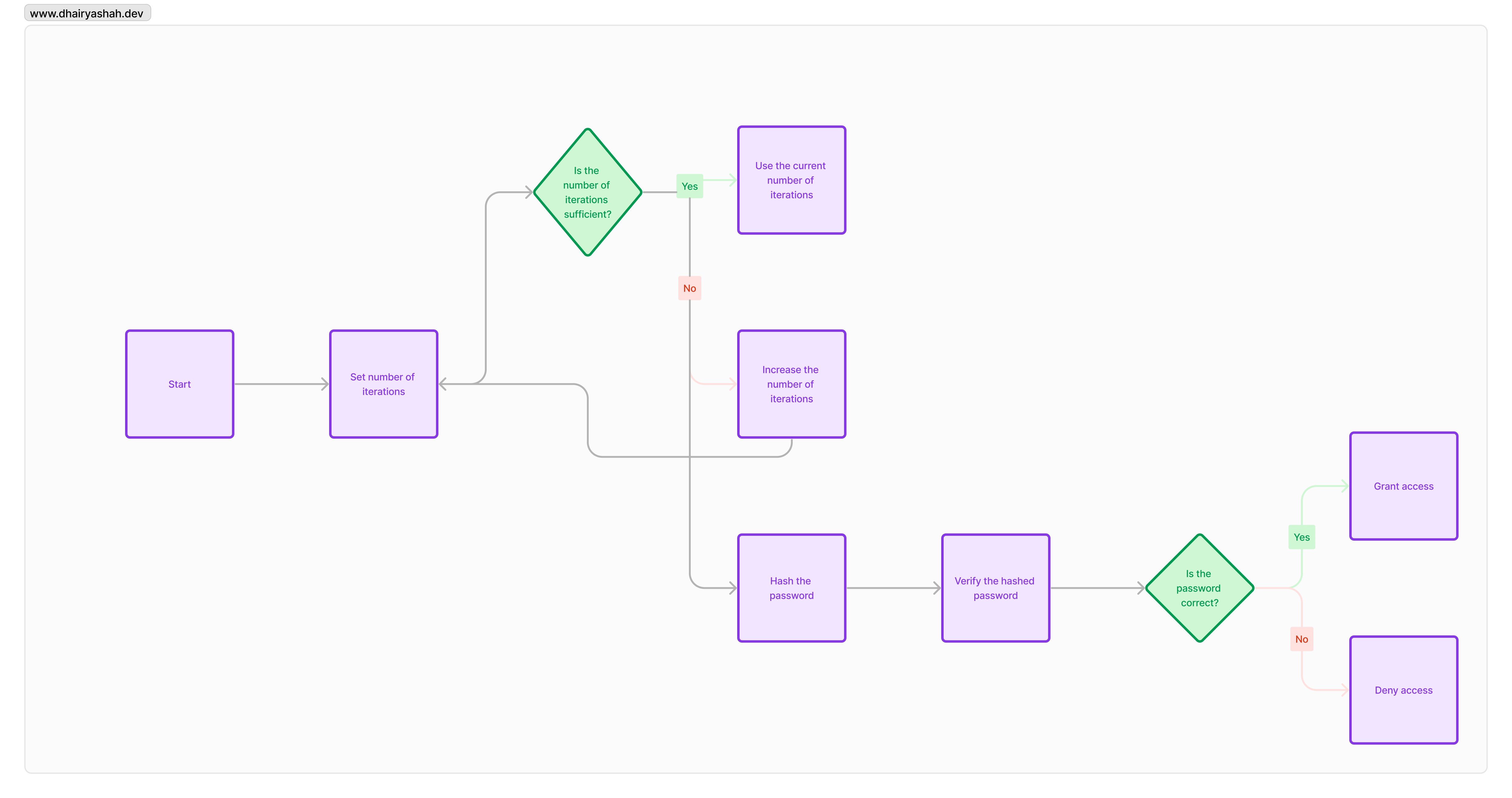
Here’s the Python code for increasing the number of iterations,
import hashlib
import os
password = b'your_password'
salt = os.urandom(16) # Generate a random salt
# Set the number of iterations (e.g., 1000000)
iterations = 1000000
key = hashlib.pbkdf2_hmac('sha512', password, salt, iterations)
print(key.hex()) # SHA512 HashThere are various other salt-hash-and-stretch algorithms, such as PBKDF2, bcrypt, scrypt and Argon2. These algorithms are extremely effective in strong the password safely in the database.
Conclusion
In conclusion, safeguarding user passwords is a critical aspect of ensuring the security of online accounts. Storing passwords in plain text is a significant risk, as a breach could expose sensitive information to malicious actors. To counteract this threat, encryption and hashing techniques play a important role.
We have seen in this article about the common techniques like brute-force attacks, dictionary attacks and rainbow tables performed by the attackers to crack the hash and access to the real password. We have also discussed about the ways to get prevented by such types of attacks by salting and increasing the number of iterations of an hash.
There’s a lot more to discuss on this topic, but let’s save it for future article.
Thanks for reading!
