Hey there, fellow tech tinkerers! As a developer and cloud enthusiast, I love messing around in my home lab—a trusty Raspberry Pi 5 running my self-hosted setup. But sometimes, I need to tap into the power of AWS for testing, dev work, or hybrid projects. In this post, I’m spilling the beans on how I bridged my home network with two AWS regions (ap-south-1 and us-east-1) using Tailscale, EC2, and VPC Peering. The result? A secure, low-latency network that feels like magic. Let’s dive in!
🧠 Why I Did This
My home lab is my sandbox for coding, experimenting, and breaking things (gently). But when I need AWS’s managed services—like serverless functions or storage—I don’t want to deal with public IPs or clunky SSH setups. My goal was to create a private, secure, and dead-simple network bridge connecting:
- My Home Network (192.168.0.0/24)
- My AWS VPC in ap-south-1 (172.31.0.0/16)
- My AWS VPC in us-east-1 (172.15.0.0/16)
No public exposure, no VPN headaches—just smooth, encrypted access from my home terminal to the cloud.
🛠️ My Toolkit
Here’s what I used to pull this off:
- Tailscale: A slick, WireGuard-based mesh VPN that connects my devices and AWS instances like they’re on the same LAN.
- Amazon EC2: A lightweight instance to relay traffic between my networks.
- VPC Peering: AWS’s way to privately link VPCs across regions.
- Linux Routing (
ip route,sysctl): Good old Linux commands to handle custom routing.
🔗 Step 1: Getting Tailscale Up and Running
First things first, I installed Tailscale on:
- My Raspberry Pi 5 (running Raspbian, because Debian is life) at home.
- A tiny EC2 instance in my
ap-south-1VPC (172.31.0.0/16).
After signing both into my Tailscale account (super quick setup, by the way), I told the EC2 instance to advertise the VPC’s CIDR block so my home network could see it:
tailscale up --advertise-routes=172.31.0.0/16 --accept-routes
Boom! My home network could now reach private resources in ap-south-1 through Tailscale—no VPN, no bastion host, just pure simplicity.
🌍 Step 2: Routing VPC Traffic Back Home
To let my home network talk to the ap-south-1 VPC, I turned on IP forwarding on the EC2 instance (because it’s gotta play traffic cop):
sudo sysctl -w net.ipv4.ip_forward=1Then, on my Raspberry Pi, I added a route to send VPC-bound traffic through the EC2’s Tailscale IP (mine was 100.104.53.61—yours will differ):
sudo ip route add 172.31.0.0/16 via 100.104.53.61

After this, I could curl or ping internal VPC endpoints from my home lab. It felt like my Pi was living in the cloud!
🌐 Step 3: Hooking Up us-east-1 with VPC Peering
Now, I wanted my us-east-1 VPC (172.15.0.0/16) to join the party. Enter VPC Peering:
- Requester VPC:
ap-south-1(172.31.0.0/16) - Accepter VPC:
us-east-1(172.15.0.0/16)
I set up the peering connection in the AWS console (pretty straightforward) and updated the route tables:
- ap-south-1 Route Table: Added
172.15.0.0/16to route via the peering connection. - us-east-1 Route Table: Added
172.31.0.0/16to route via the peering connection.

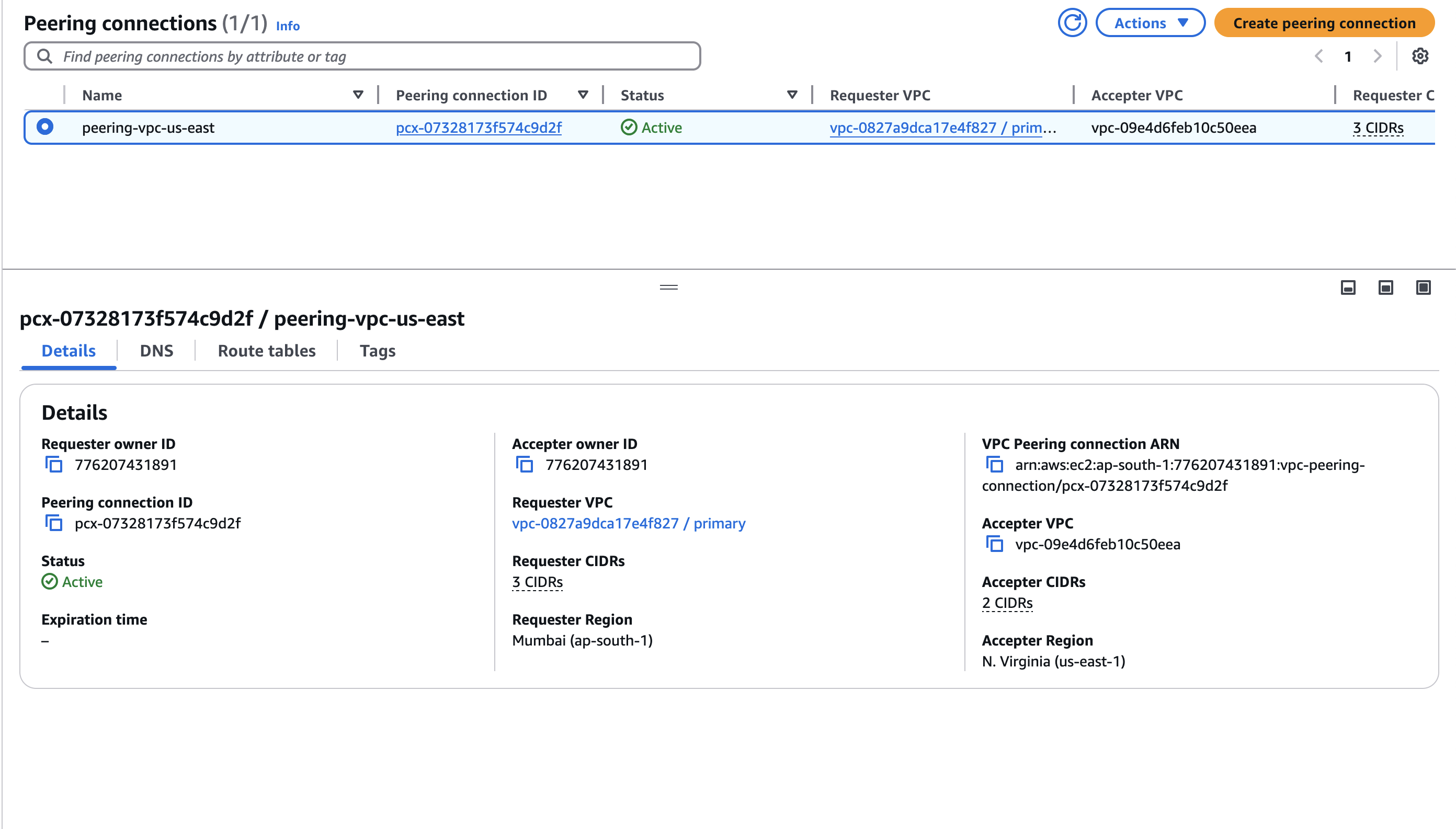
This let my EC2 instance in ap-south-1 talk to us-east-1 resources. To make us-east-1 accessible from my home network, I updated the EC2’s Tailscale route advertisement to include both VPCs:
tailscale up --advertise-routes=172.31.0.0/16,172.15.0.0/16 --accept-routesNow my home lab could reach both AWS regions through the EC2 relay. Mind blown!
🔒 Locking It Down
Security’s a big deal, so I made sure to:
- Tighten Security Groups: The EC2 instance only allows Tailscale traffic (UDP 41641, TCP 443) and internal VPC traffic.
- Skip Public IPs: No NAT gateways or Elastic IPs here—everything’s private and cost-effective.
- Use Tailscale ACLs: I set up access controls in the Tailscale admin console to limit which devices can access which CIDRs. Only my trusted devices get through.
✅ What It All Looks Like
Here’s the final network setup:
+-----------------------------+
| Home Network (LAN) |
| CIDR: 192.168.0.0/24 |
| Devices (Raspberry Pi, |
| Laptop, etc.) |
+-------------+---------------+
|
(Tailscale VPN Tunnel)
|
v
+----------------------------+
| EC2 Relay Instance |
| Region: ap-south-1 (Mumbai)|
| Private IP: 172.31.x.x |
+-------------+--------------+
|
+--------------------------+---------------------------+
| |
v v
+------------------+ +----------------------------+
| ap-south-1 VPC | | VPC Peering Connection |
| CIDR: 172.31.0.0/16 |<--------------------->| us-east-1 VPC |
| Internal Services | | CIDR: 172.15.0.0/16 |
| or Subnet A | | Backend / Analytics |
+------------------+ +----------------------------+
It’s all private, encrypted, and surprisingly fast—no VPN appliances or public NAT nonsense.

🎯 Wrapping Up
Setting this up has completely transformed my dev workflow. I can now access AWS resources from my home lab just like they’re part of my local network. Tailscale makes hybrid networking super smooth, and VPC Peering keeps traffic between regions fast and private.
If you’re thinking about connecting your home lab to the cloud, I highly recommend giving this a shot—it’s secure, scalable, and honestly, kinda fun to build.
Got questions or cool tips of your own? Let’s chat in the comments or feel free to reach out. Happy networking! 🚀
